In today's world of permanent Internet connectivity, whether through Wi-Fi or Ethernet, a firewall is an essential component of your device's security. This software – or in some cases, a separate physical device – monitors all incoming and outgoing network traffic to and from your computer, including any program attempting to access the Internet.
Microsoft Windows has included a built-in firewall for many years. For most users, there's no need for intervention – it's activated by default and configured for general use. But what if you wish to prevent a specific application from connecting to the Internet, or if you want to block a particular IP address from accessing your PC?
This practical guide will show you how to accomplish these tasks, so you can manage your firewall settings effectively.
Finding the Windows Firewall
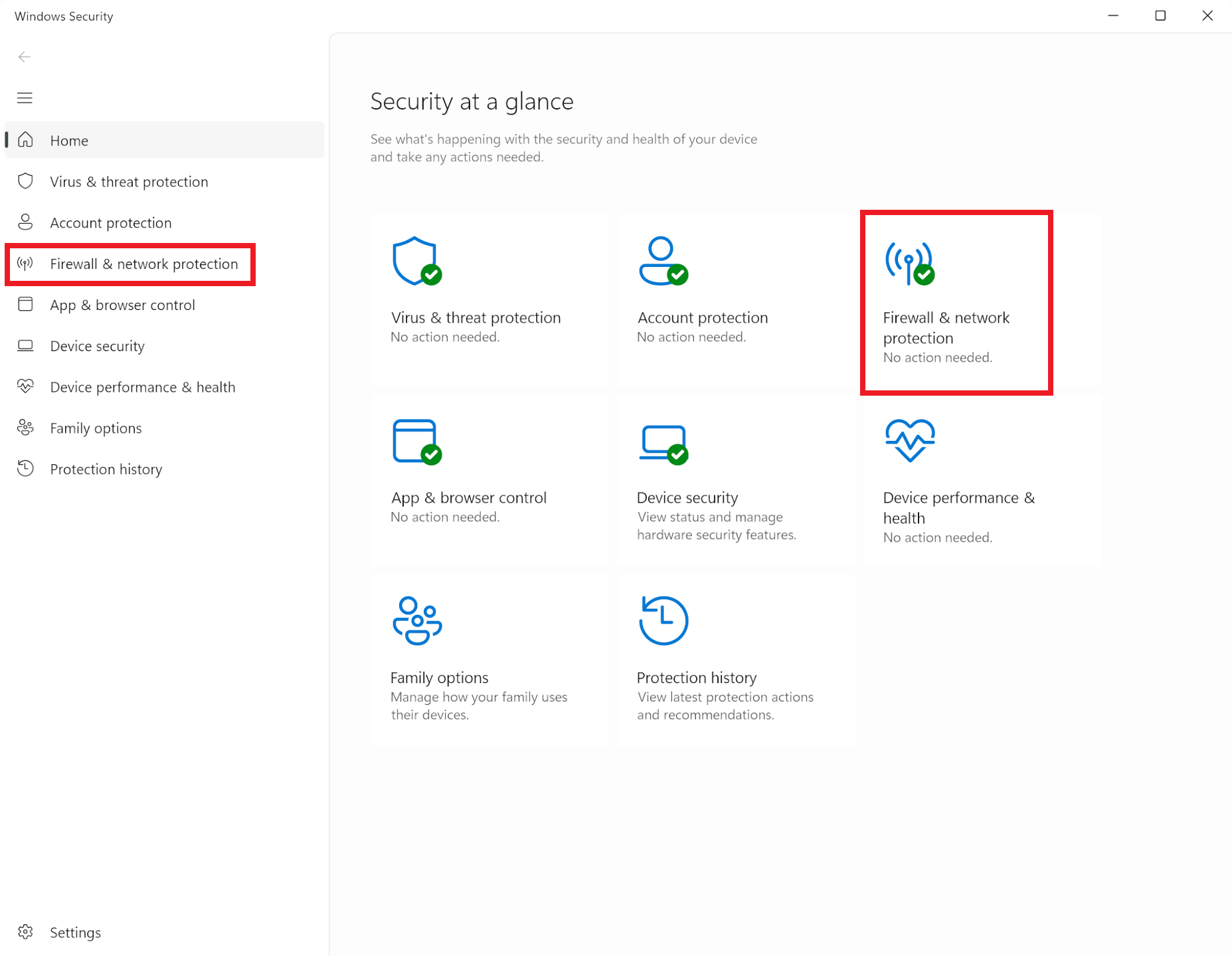
Click on Start and type "Windows Security" – within a few letters, you should see an application with that name shown in the search results (the icon looks like a big, blue shield).
Clicking on this will open the Windows Security hub.
From here, you can access the firewall by selecting 'Firewall & network protection' from the list on the left-hand side or by clicking the corresponding icon in the main menu. Once there, you'll see three types of networks that the software monitors: domain, private, and public.
Unless your PC is part of an Active Directory Domain, the domain network setting will not be applicable – it's typically utilized by large organizations to manage numerous computers and user accounts across extensive networks. In such environments, you are unlikely to have firewall control.
This brings us to the private and public network settings. For most people, the default setup when connecting their PC to the Internet is as a public network. This setting ensures that the PC is concealed from other network users, which contrasts with the visibility within a private network. The private setting should be used exclusively for a network that is not accessible to devices outside of your trusted group of equipment.
As illustrated in our example, we are connected to a public network, but the built-in firewall is automatically configured to monitor all types of networks.
The software follows an extensive set of rules to control the incoming and outgoing data for each application or OS service. By modifying these rules or adding new ones, we can instruct the firewall to block a specific program from accessing the Internet, for example.
It's important to note that if you are utilizing a standalone antivirus package with its own firewall, this will take precedence over Windows' firewall settings. In such a case, you would need to navigate the antivirus software's settings to make any changes. However, this guide is focused on the Windows 11 firewall, so let's proceed to learn how to block both outgoing and incoming data.
Blocking a program's outgoing network access
Windows typically allows any program to send data freely, as there's usually no need to block this activity. Suppose, however, there's a good reason to prevent a particular application from accessing the Internet.
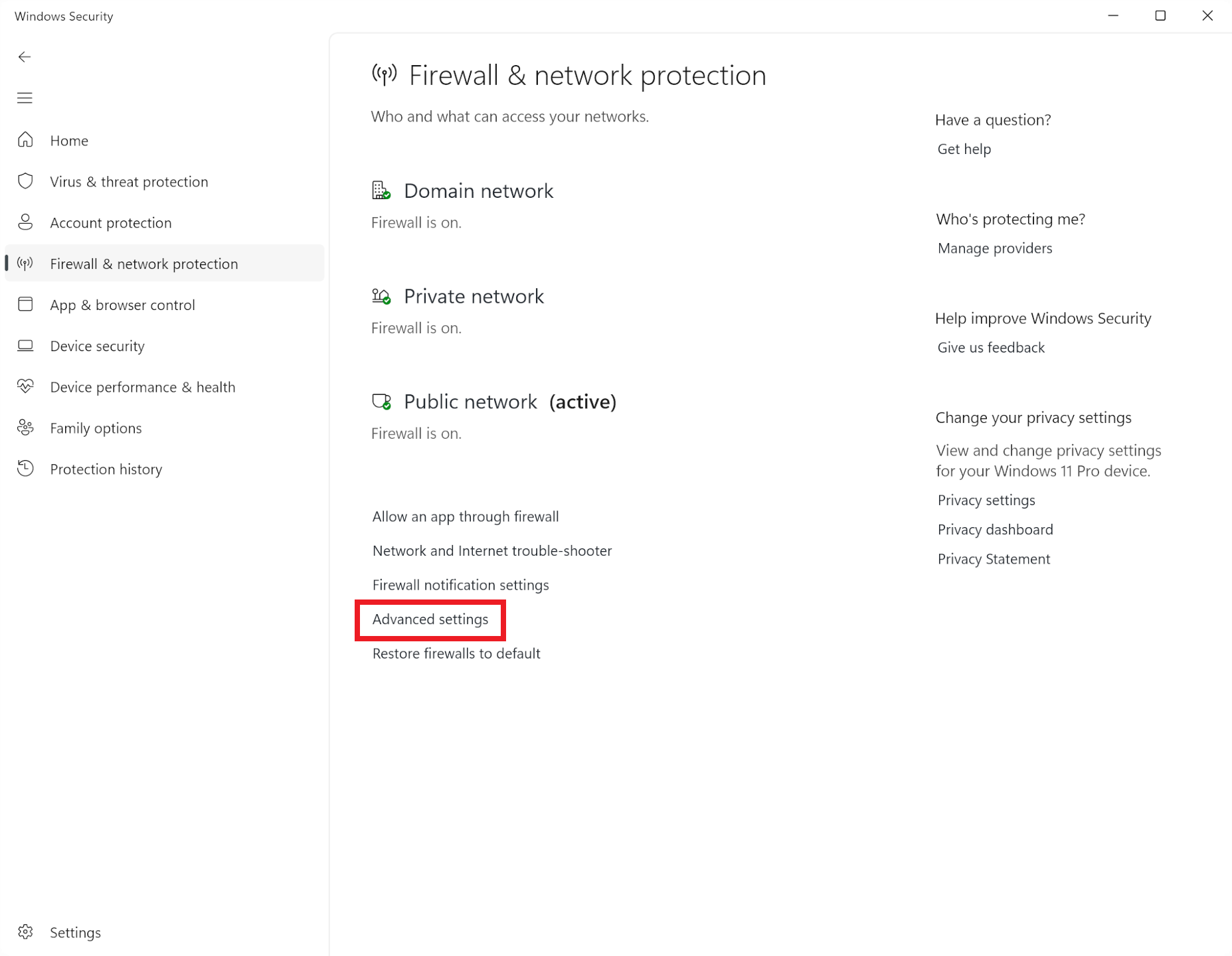
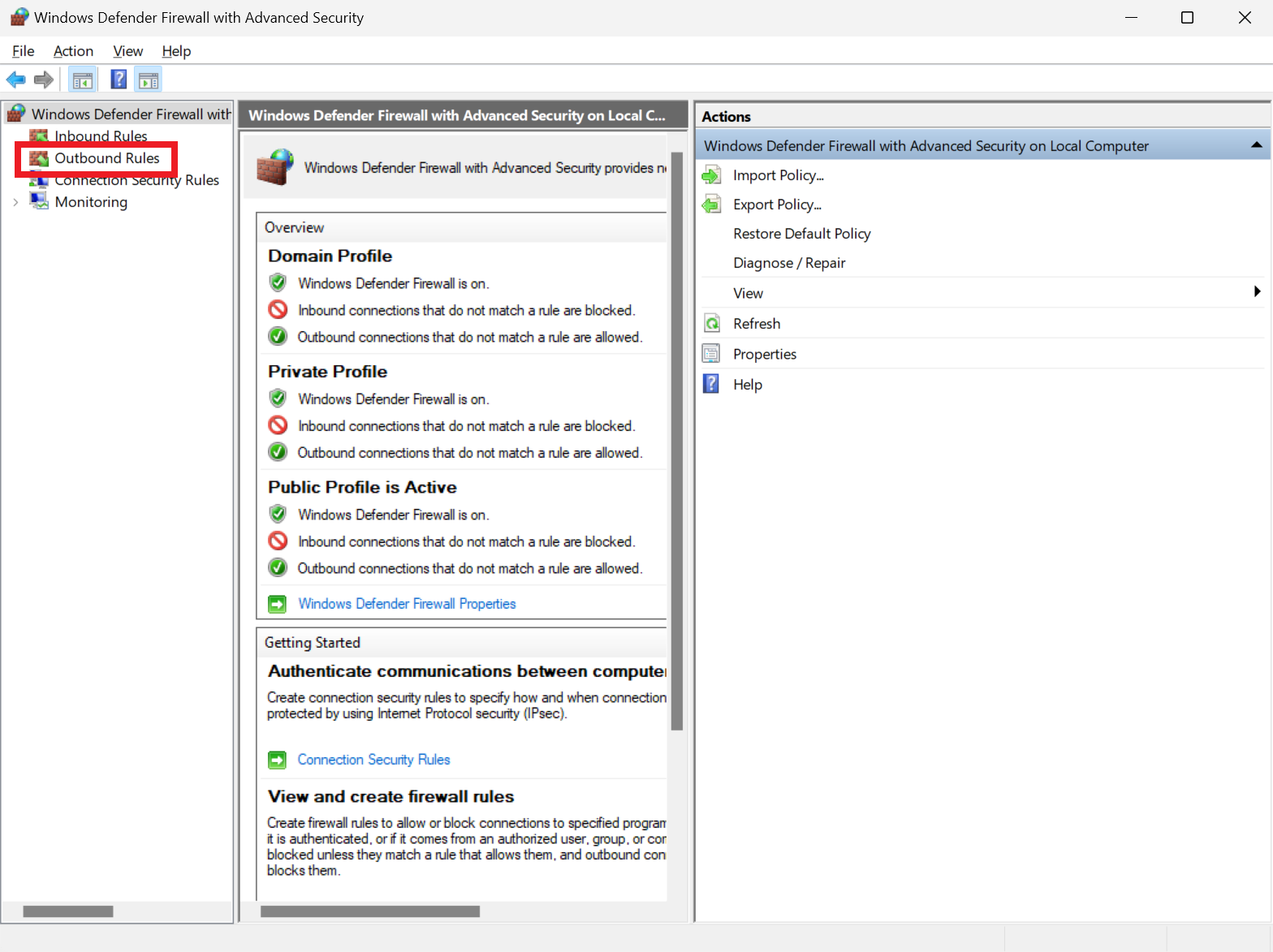
To do this, we create a new rule specifically for that program. In the firewall's main menu, as depicted earlier, click on the 'Advanced settings' located near the bottom. A busy-looking window will open, but most of it can be ignored – simply select 'Outbound Rules' from the top of the left menu or the middle pane.
You'll then see a lengthy list of rules, each corresponding to a program or service with network access. If there are multiple user accounts on the PC, you might find duplicate rules for each account if a program has been installed for every user.
A green tick on the left of each line indicates that the firewall isn't blocking that particular access. The rules detail the network types they apply to, the actions they perform, whether they can be overridden, and so forth – the information provided is quite detailed.
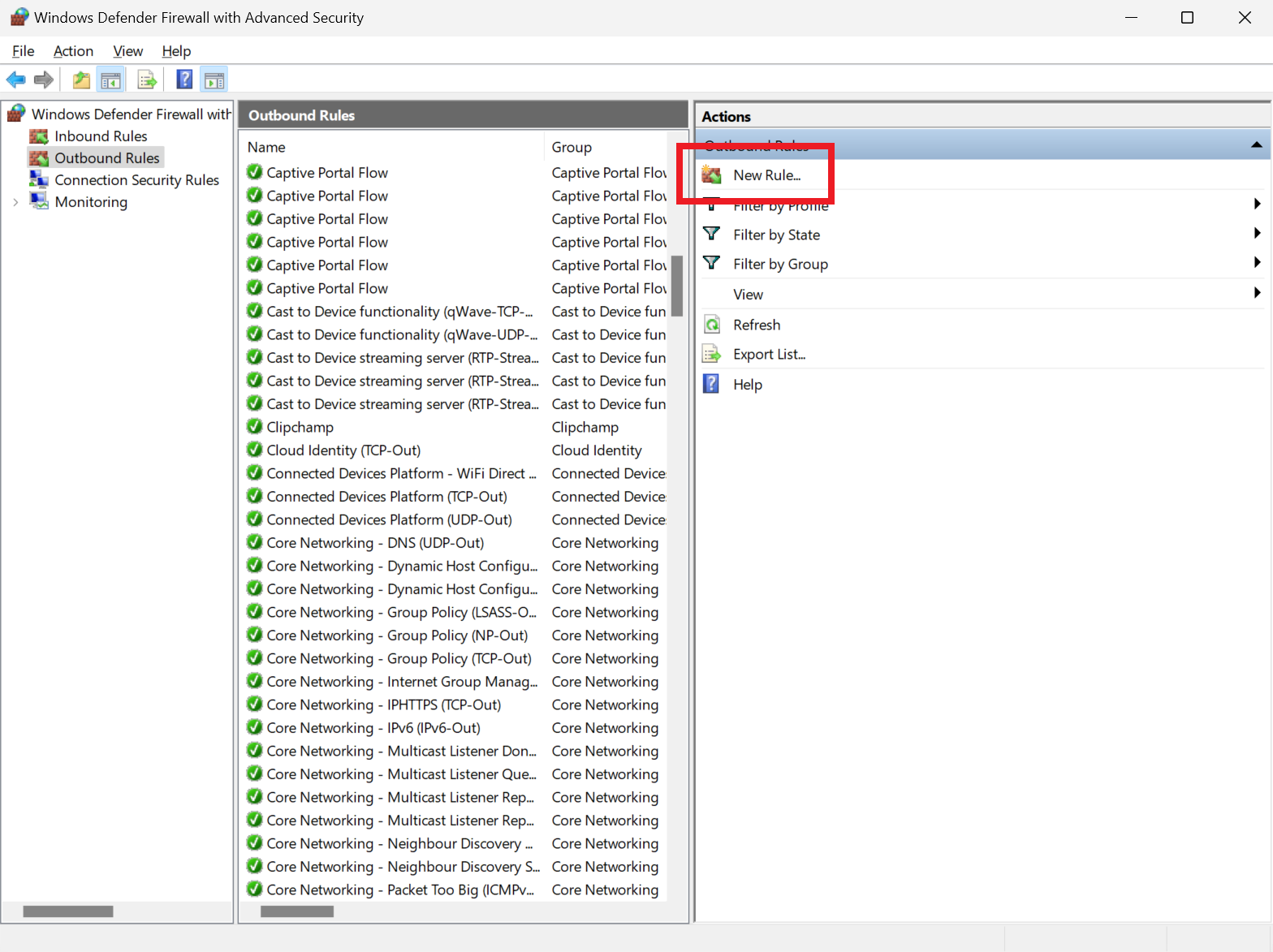
Although this all looks complex (because it kind of is), adding a new rule to block a program's network access is fortunately very simple.
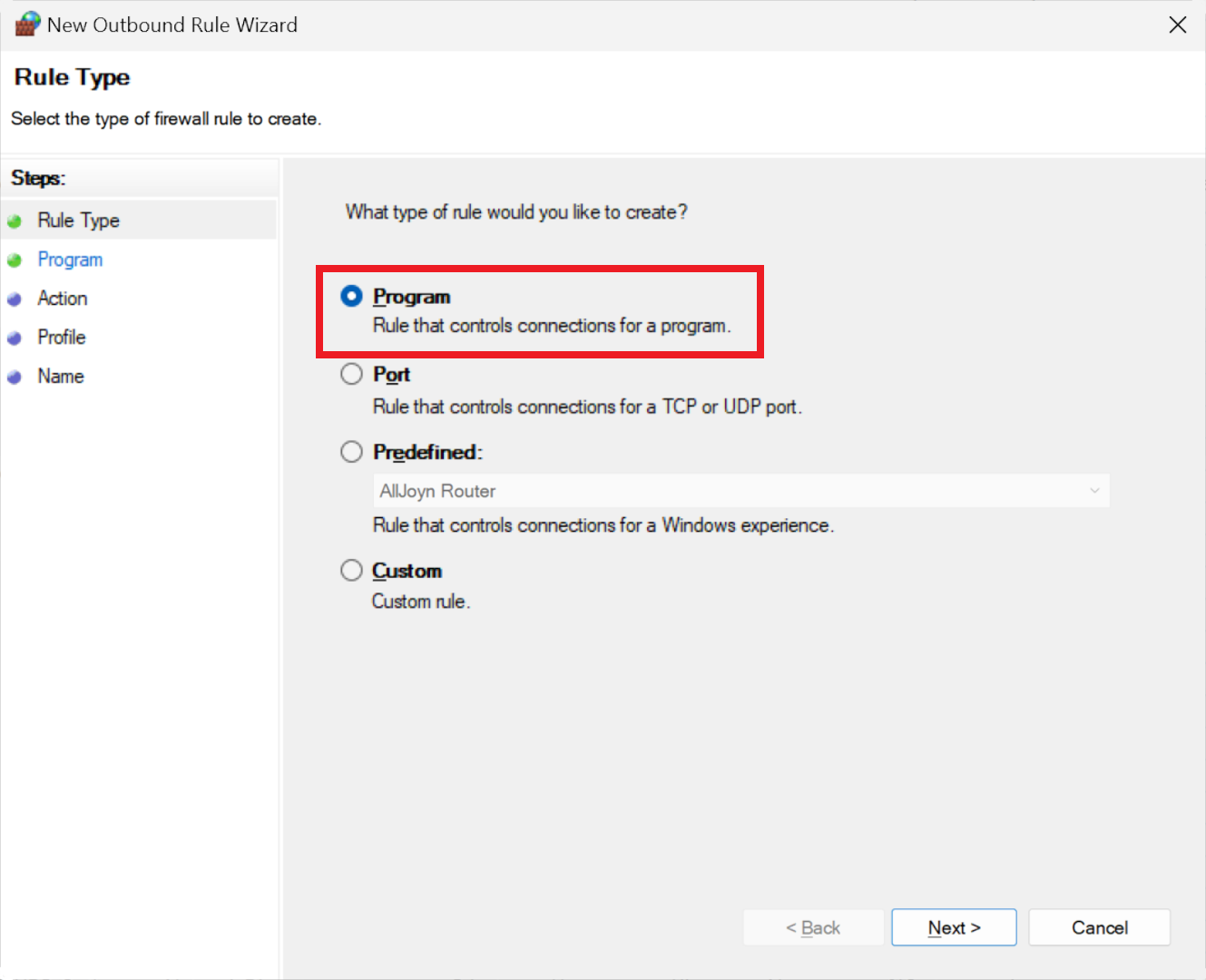
Click on 'New Rule...' at the top of the right pane. This will launch a wizard that guides you through the rule creation process. Before beginning, you need to know the exact name of the program you're going to block and where it's located on your drive.
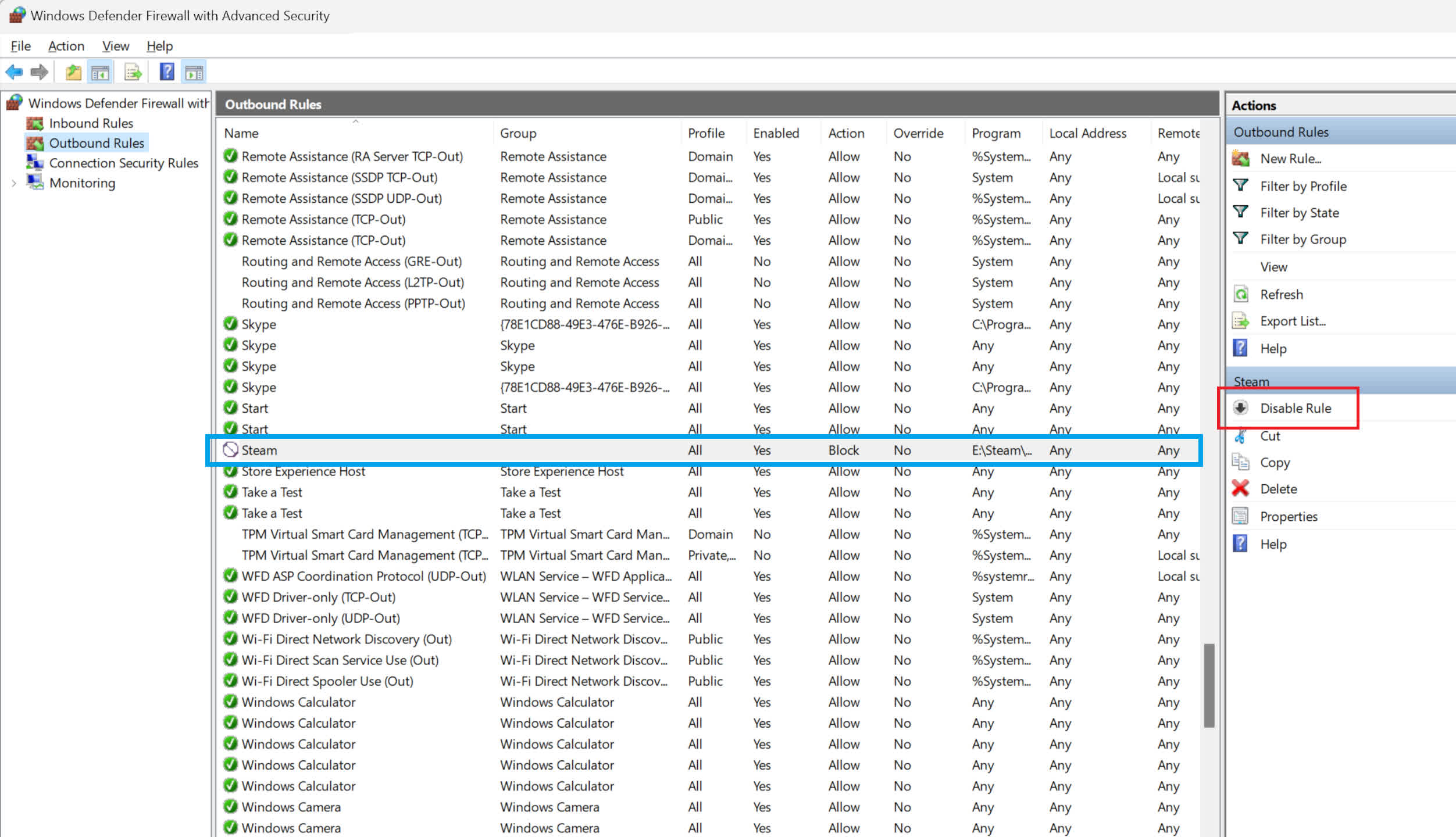
For demonstration purposes, let's block the main Steam executable file. It will still allow login (as it utilizes a separate utility for that), but the block will prevent uploading any files, like cloud saves, screenshots, or game achievements. This is merely an example for instructional purposes, and there's typically no practical reason to block Steam in this manner, but it serves as an easy example on our test system.
The first step of the Outbound Rule wizard is straightforward – we want to block a program, so use the first option, and then click on the Next button to procedure the second stage.
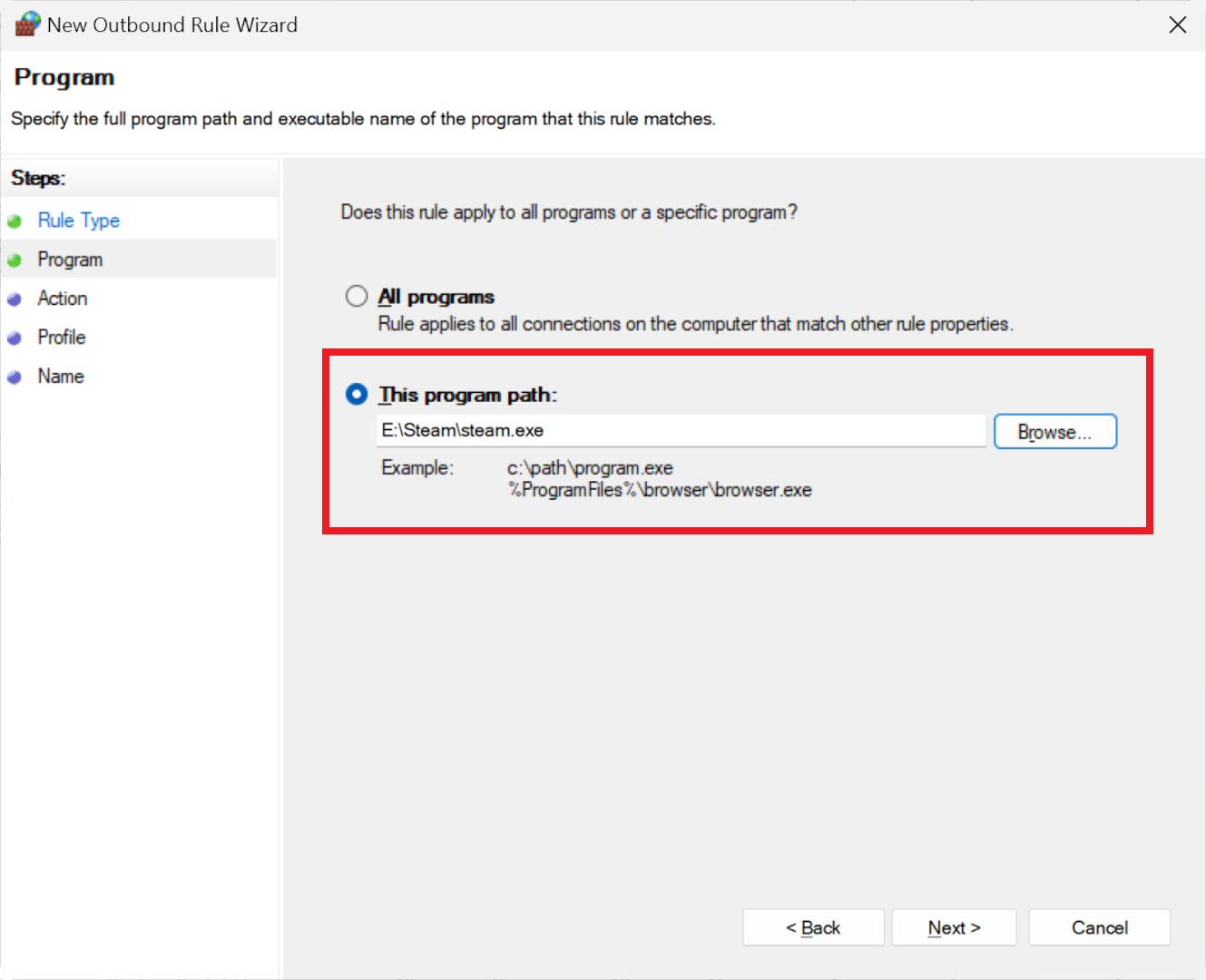
Choose the option labeled 'This program path:' since we aim to control a specific application, and then input the file's location. You can either provide the exact path, or you can use a more general approach as the wizard's example shows, employing the % symbols, which removes the need to specify the drive where the file is stored.
Make sure you select the correct file. If you choose a file with a different name or location than the one launched from the Start Menu or desktop shortcut, the rule won't apply to the intended program.
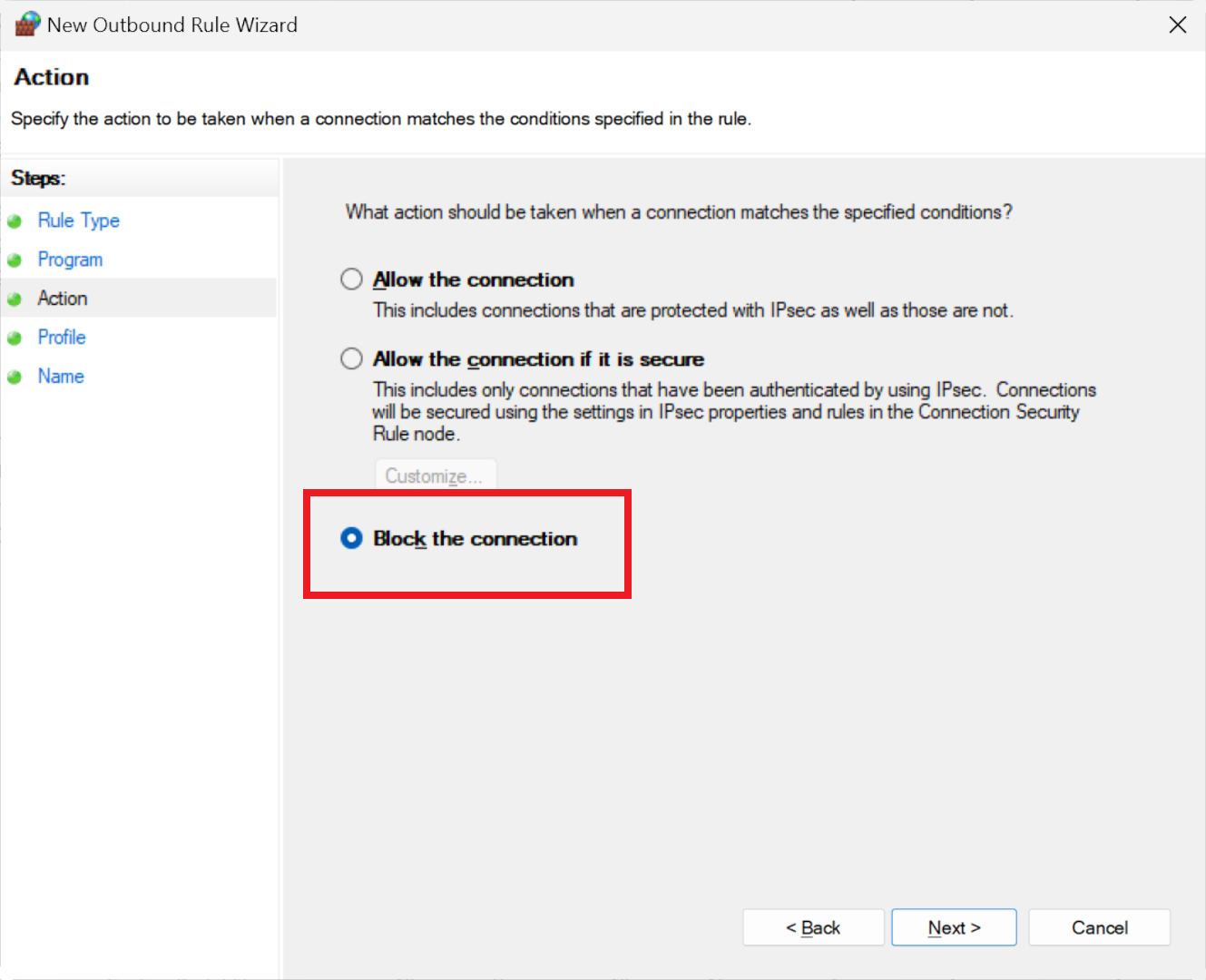
In the next step, confirm what action the rule will enforce. The 'block' option should be pre-selected, but if not, choose this option before proceeding. The subsequent stage, concerning network types the rule will apply to, can be bypassed since all are selected by default.
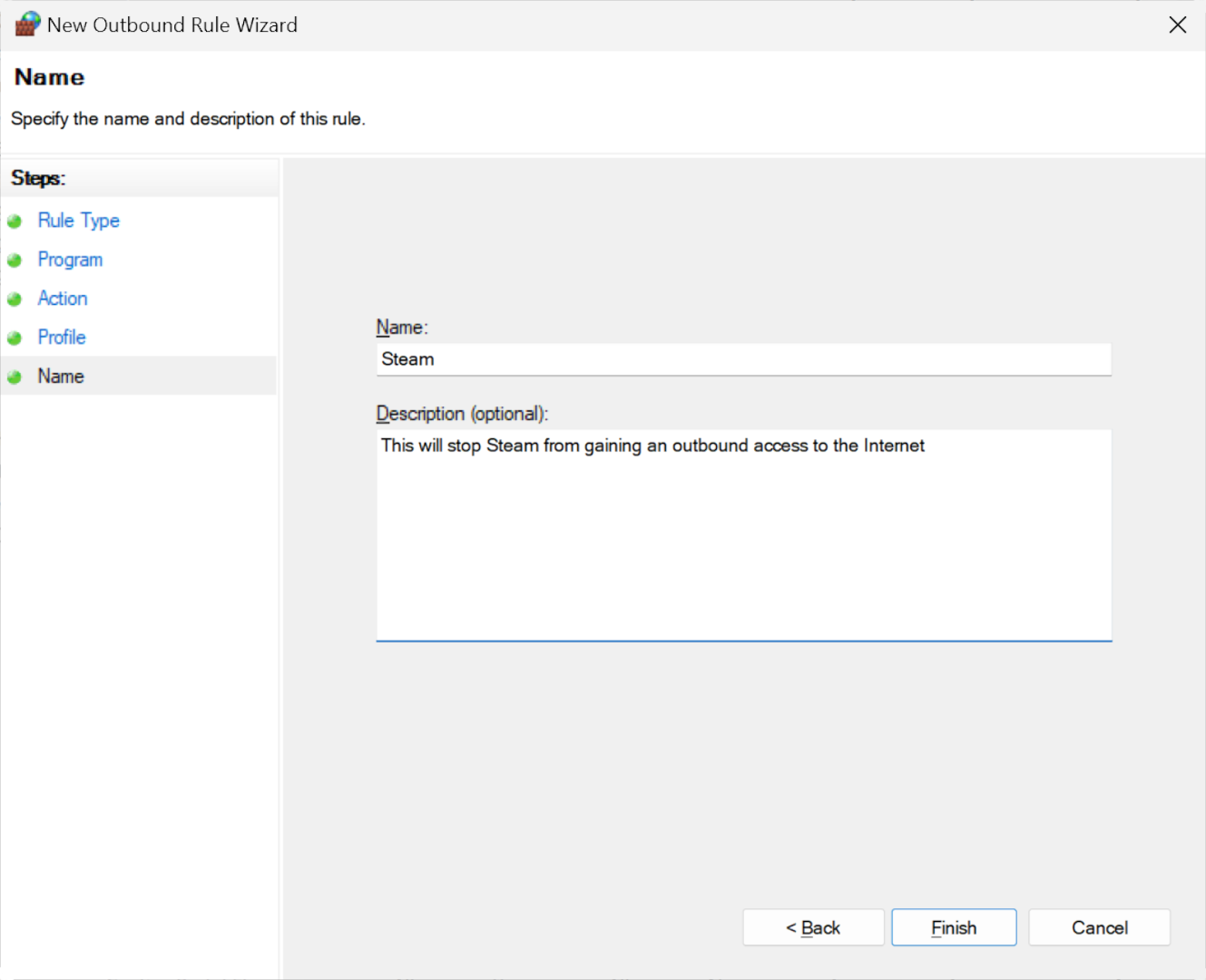
The final step involves naming the rule and providing an optional description for your own reference. After finalizing your inputs, click the 'Finish' button, and you'll return to the list of Outbound rules.
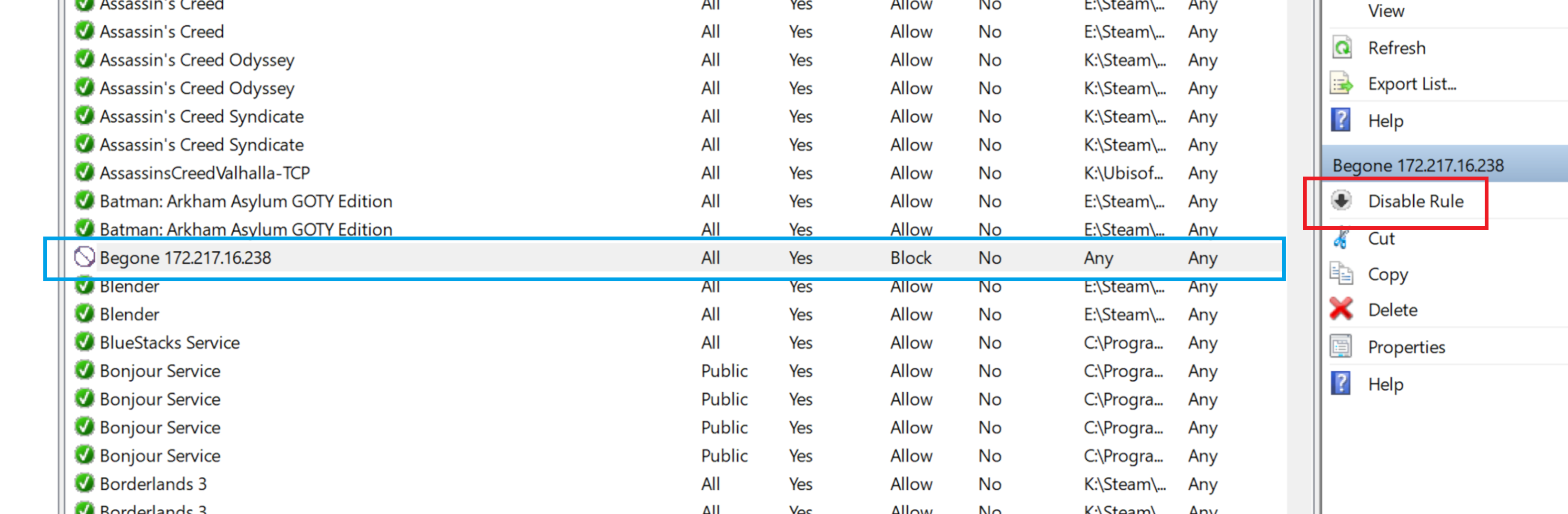
A system restart isn't necessary; your new rule is effective immediately, although locating it in the list may require some scrolling. Notice the absence of a green tick next to our Steam rule – the 'no entry' icon indicates that the program is blocked from sending data over any network the computer is connected to.
When you select the rule, the details appear in the right pane. Using the 'Disable Rule' option will deactivate it, while 'Delete' will remove it altogether.
And that's all you need to do in order to block any program from transmitting data over a network. In our Steam example, we can still log in because it uses a separate executable for that function.
This is something worth noting. If you want to completely restrict Internet access for an application that utilizes multiple executable files, you'll need to create a separate rule for each one.
Blocking incoming access to your PC
Block incoming network access, such as from a specific IP address, is similar to blocking outgoing application access. This address could belong to another device within your network or to a website or server on the Internet.
In the Firewall > Advanced settings window, select Incoming Rules instead of Outbound Rules. Overlooking the extensive list, initiate the rule-creation wizard by selecting 'New Rule...'.
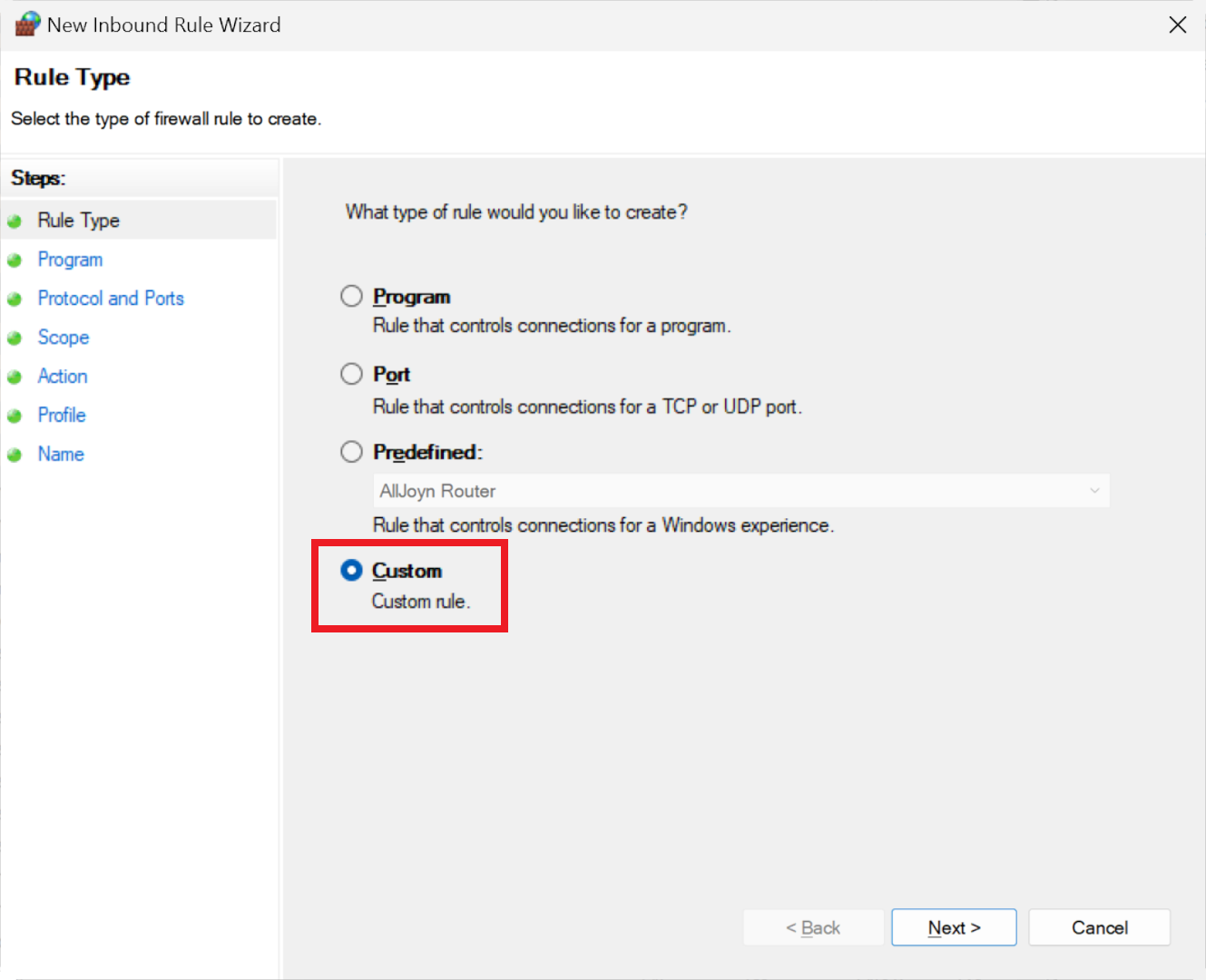
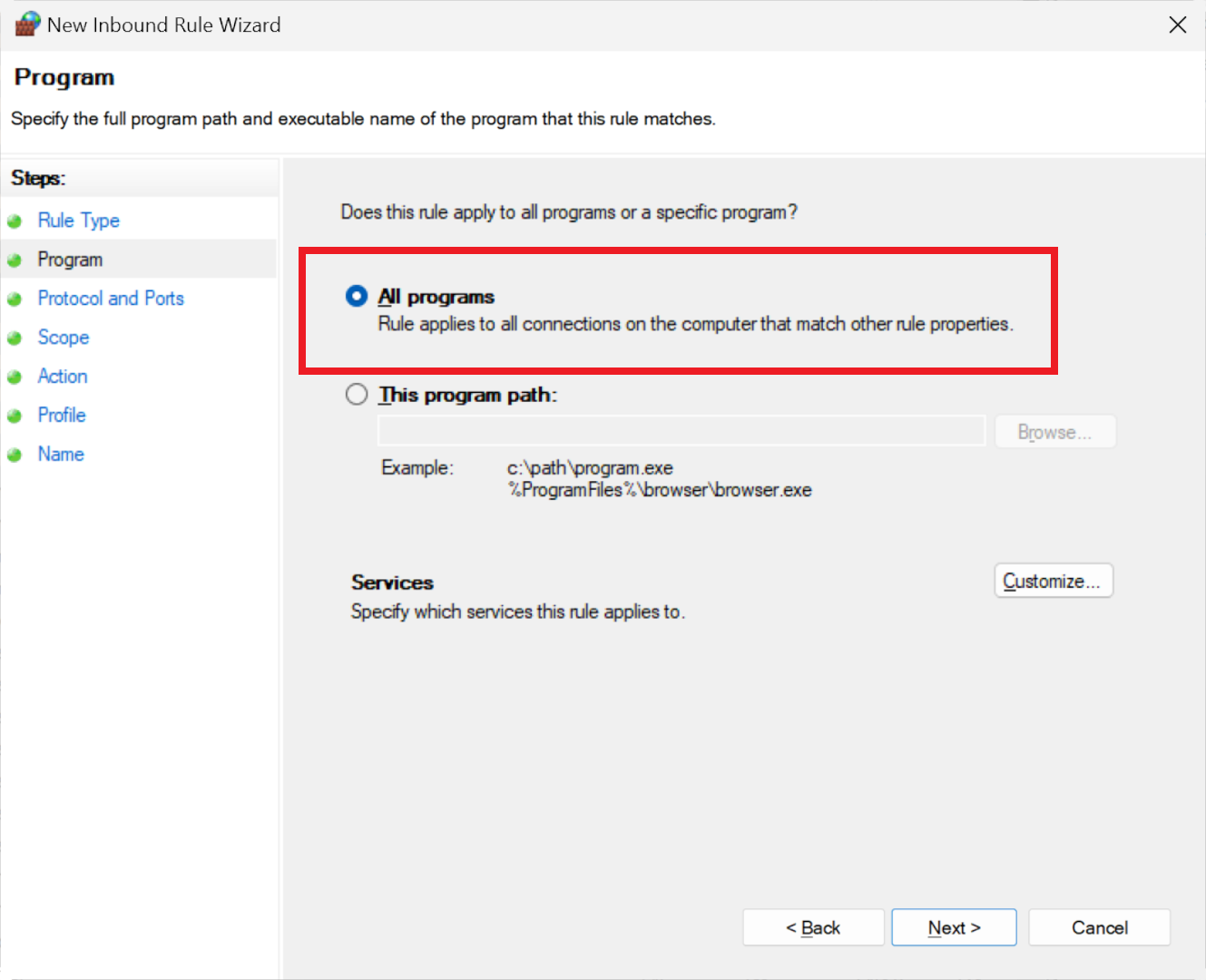
This time, opt for a 'Custom' rule on the wizard's first step to gain complete control over the necessary configurations. Ensure 'All programs' is selected, which will prevent any application or service from accepting incoming data from the IP address you will specify.
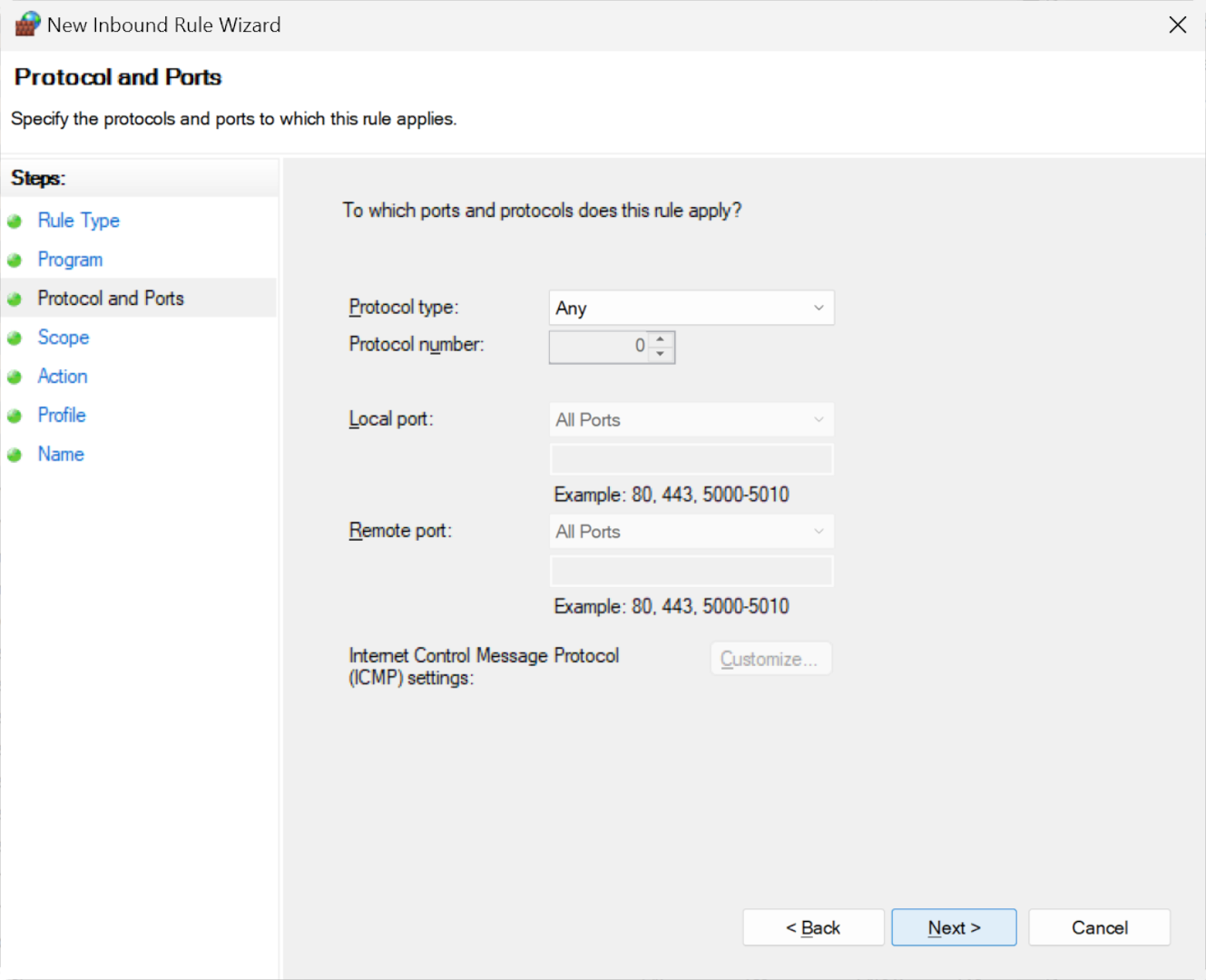
Proceed without altering the default values in the ports and protocols section to ensure the block is comprehensive.
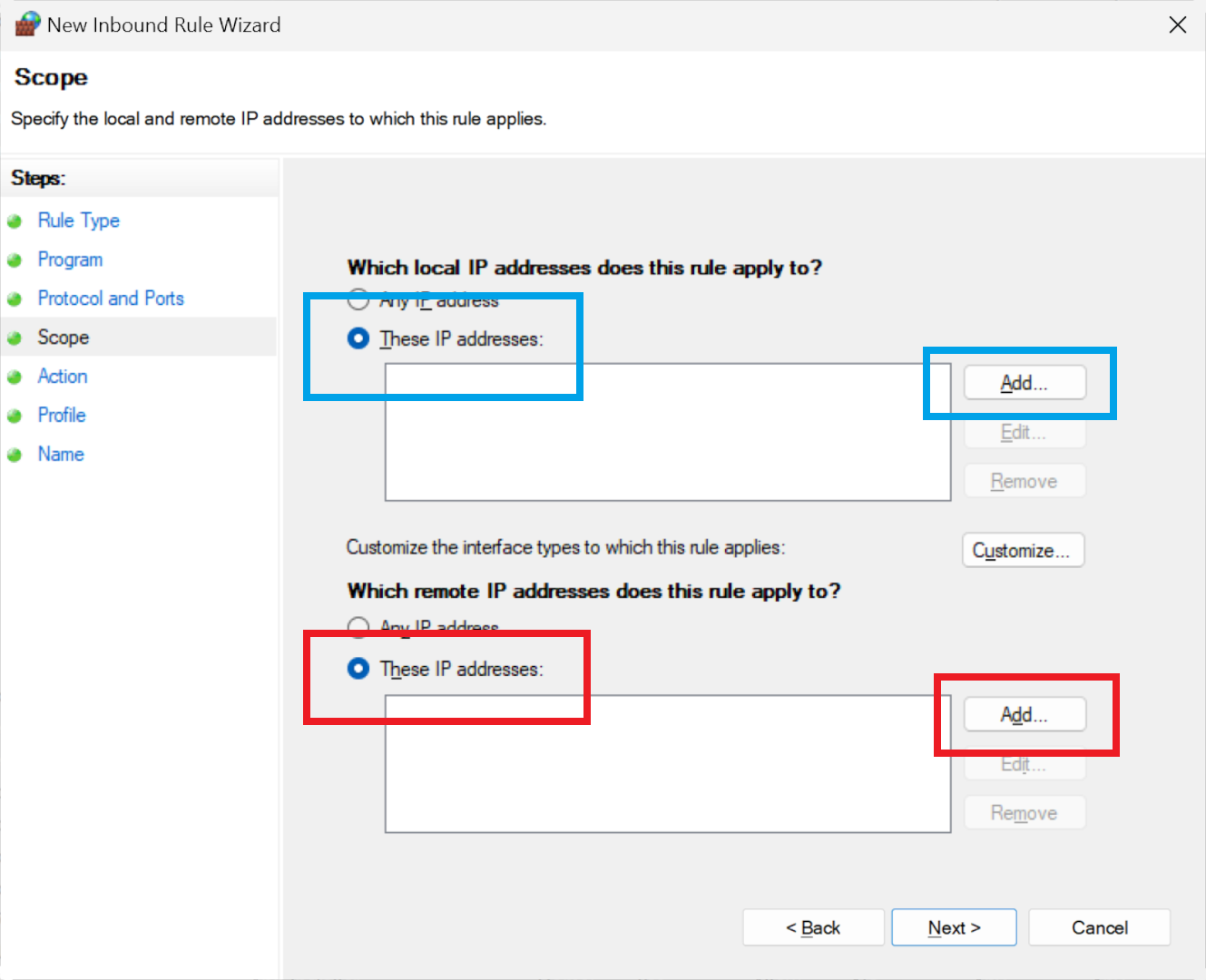
When you reach the IP address input, you can specify a single address or a range. For local network restrictions, use the 'local' option; for external IP addresses, choose 'remote'. Remember to select 'These IP addresses' to prevent a blanket block on all IPs.
The remote option covers IP addresses that are external to your local network. A PC that connects to a broadband router would be local, whereas everything on the Internet would be remote. You'll need to select the option labeled 'These IP addresses', otherwise every IP address will be blocked.
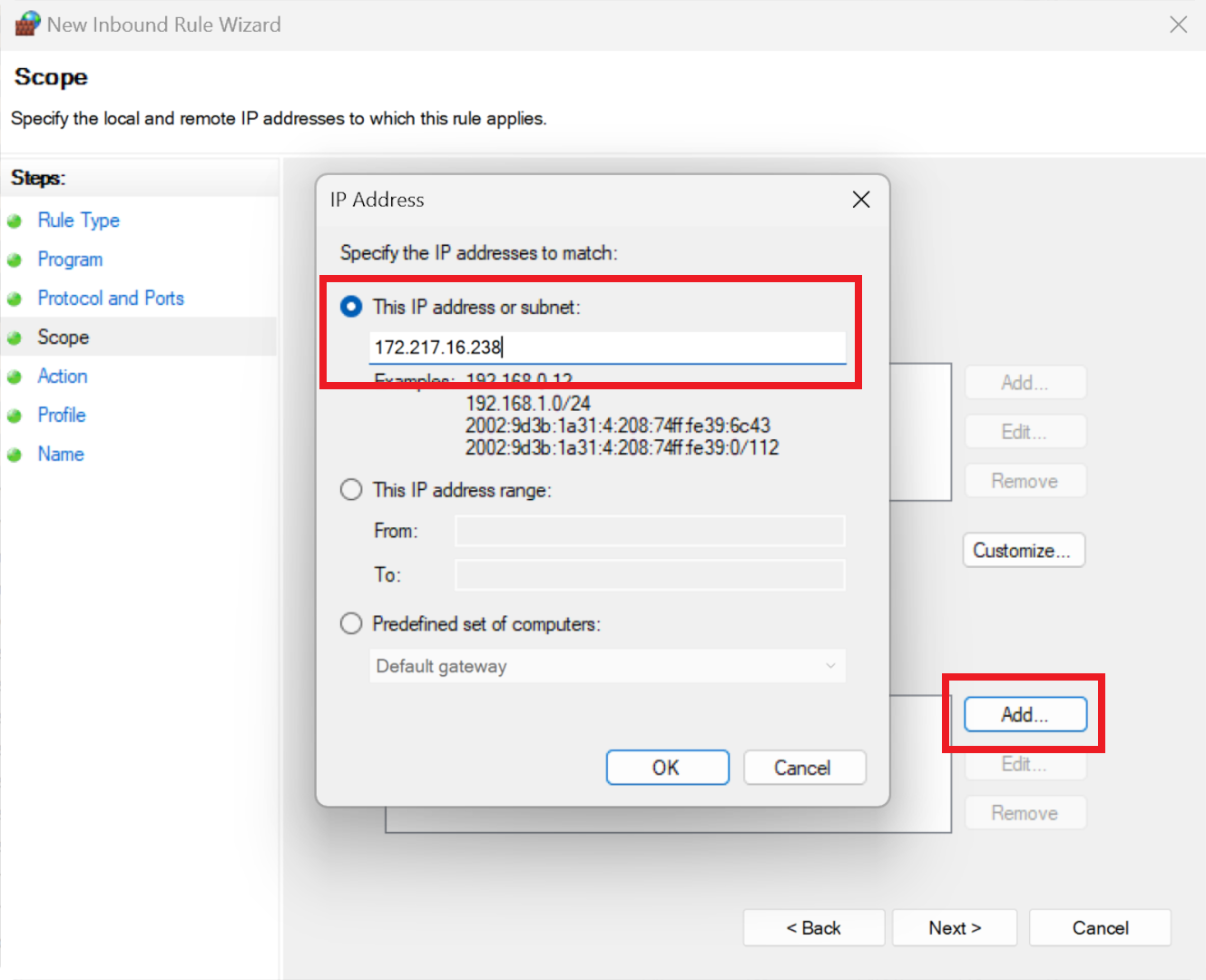
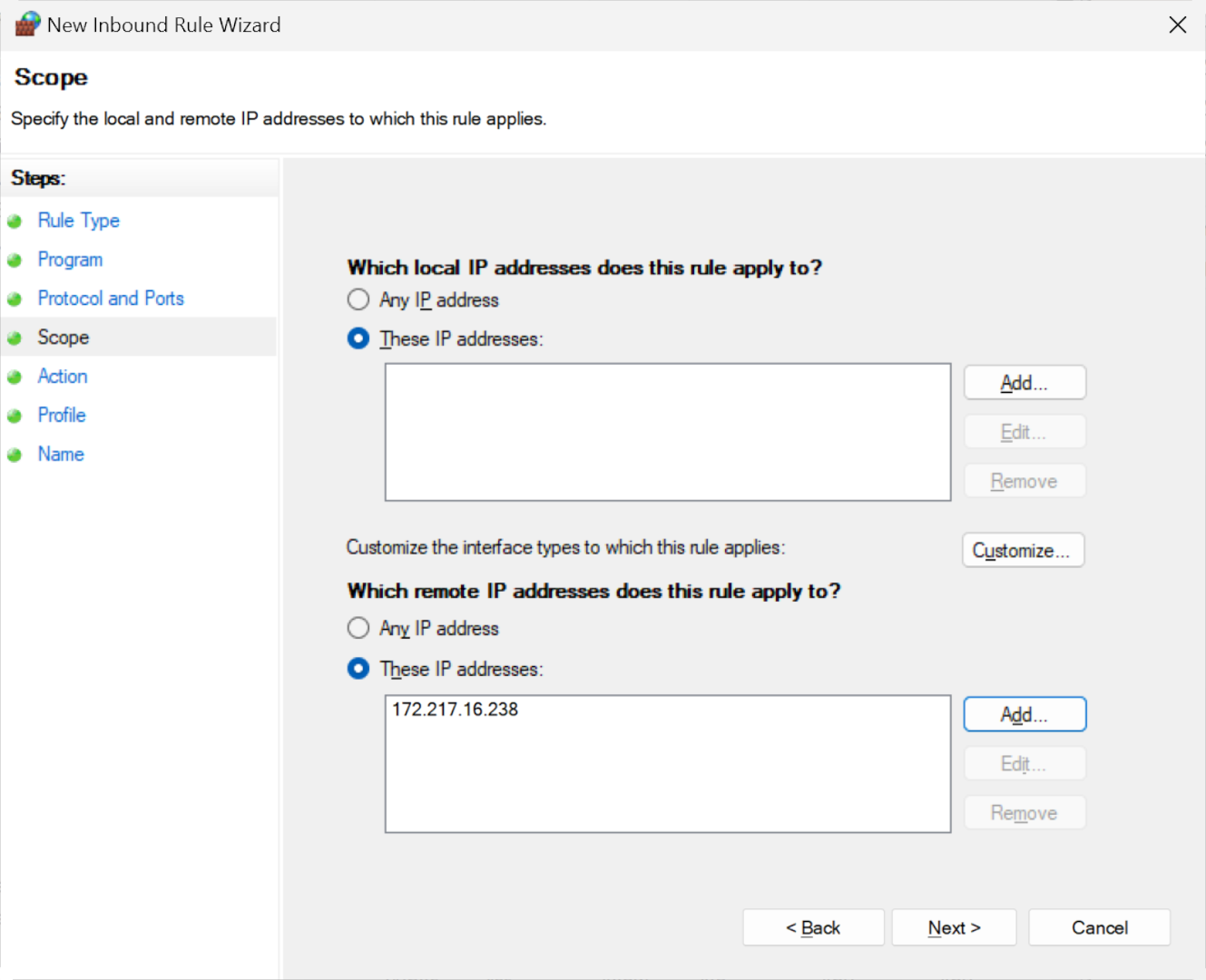
Click 'Add...' to input a singular IP address or a range. For example, you could specify a range from 172.217.16.235 to 172.217.16.240. To add multiple individual addresses, repeat the add-and-enter process as needed.
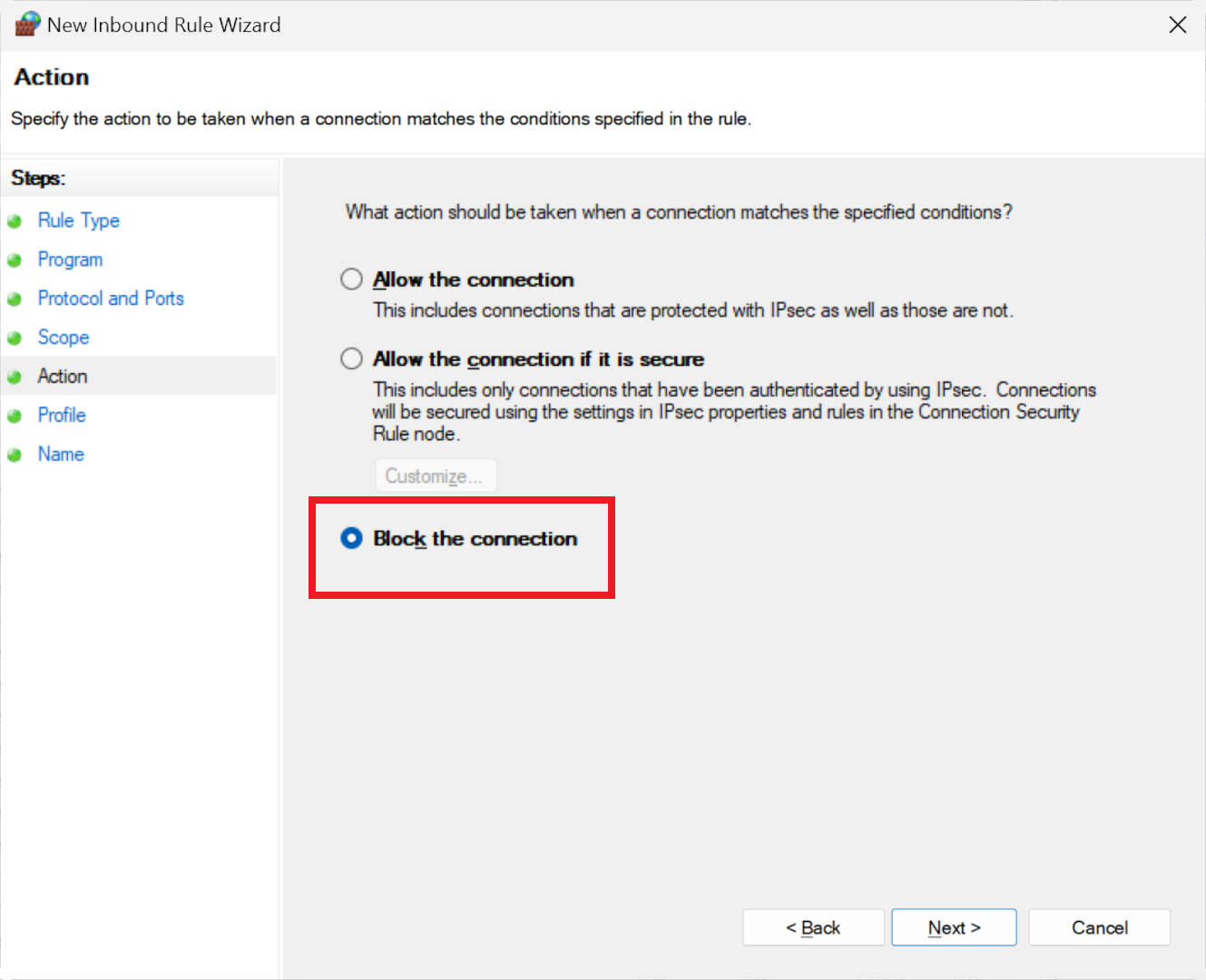
Next, specify the action – select 'Block' to prevent incoming traffic from the designated IP addresses. Note that, unlike outbound rules, the default action for new inbound rules isn't to block, so don't overlook this step.
You can skip the network type selection as it defaults to all types. Finally, name the rule and, if desired, provide a description. The rule will be active immediately upon completion.
The new rule can be disabled (see the red highlight above) or deleted if necessary. However, be certain of the IP address you're blocking. For instance, websites often don't use a single, static IP address, so blocking one may not prevent access.
For home networks, where devices can be assigned fixed IPs, an Inbound Rule is an effective way to restrict access.