What just happened? A government review of the attack on Microsoft's Exchange Online hosted email service by a China-linked group has blasted the Redmond company for allowing a "cascade of security failures" that were preventable and should never have occurred. The report describes Microsoft's security culture as "inadequate" and requiring an overhaul.
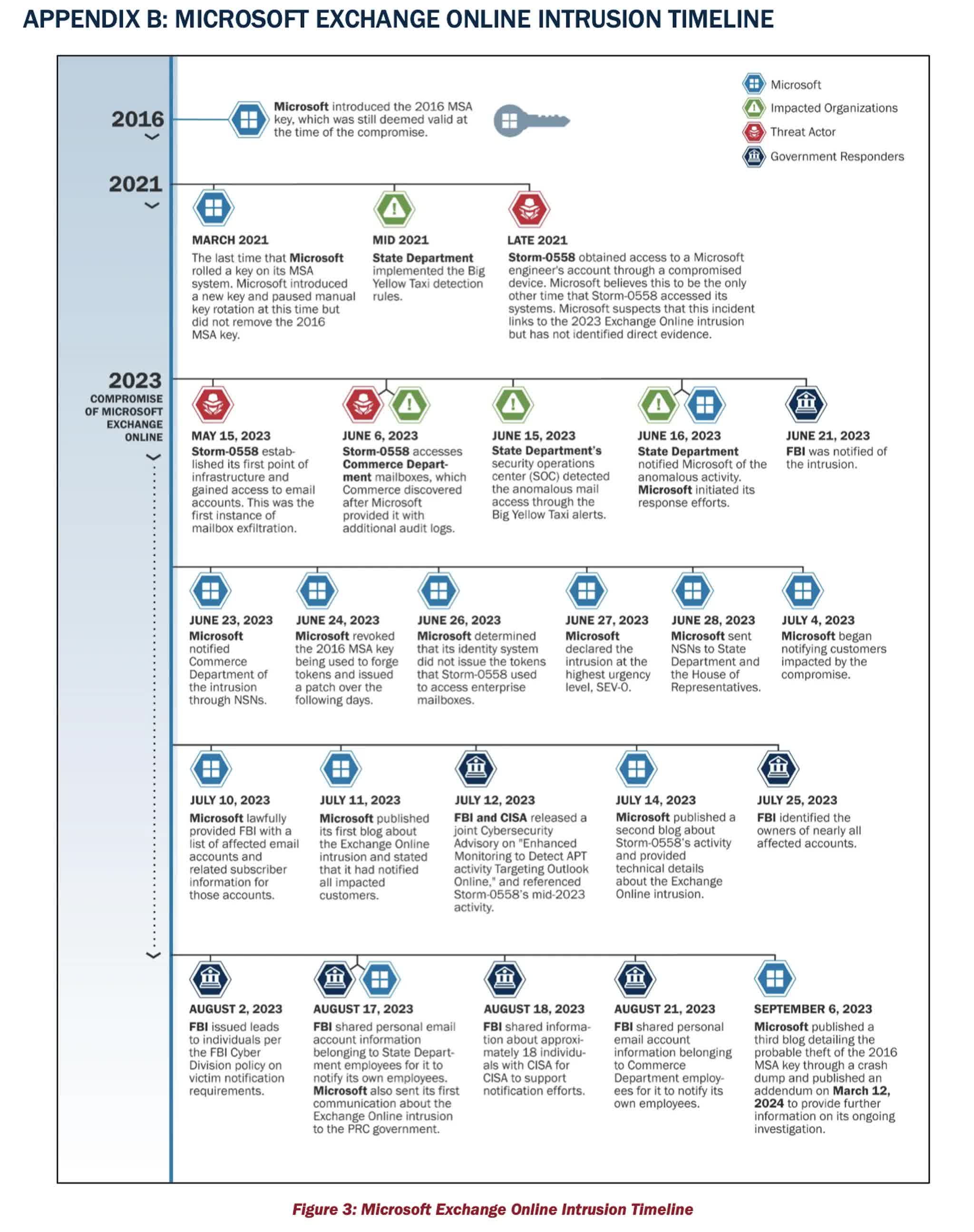
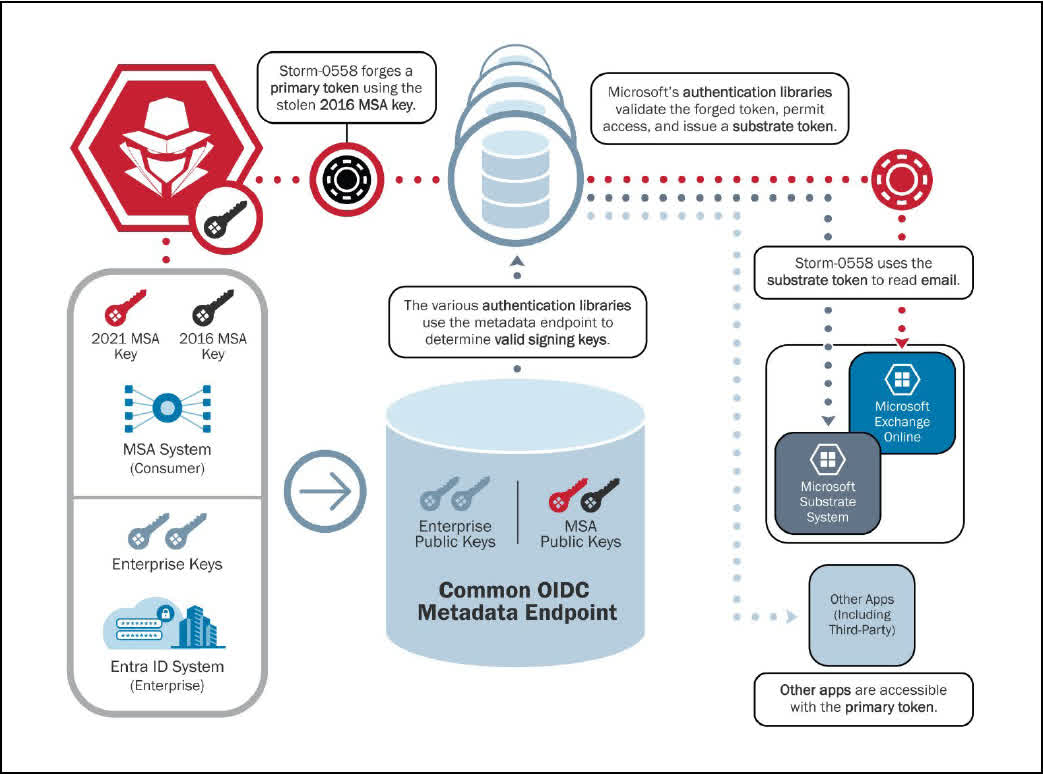
The Exchange Online hack that took place last May is believed to have been linked to a China-affiliated threat actor known as Storm-0558 stealing an Azure signing key in late 2021 from an engineer's compromised laptop that came into Microsoft's possession after an acquisition.
The hack allowed those responsible access to the online email inboxes of 22 organizations, affecting more than 500 people, including Commerce Secretary Gina Raimondo, US Ambassador to the People's Republic of China R. Nicholas Burns, Congressman Don Bacon, and Assistant Secretary of State for East Asian and Pacific Affairs Daniel Kritenbrink.
A review of the incident carried out by US government's Cybersecurity and Infrastructure Security Agency's Cyber Safety Review Board (CSRB) states that the hack was "preventable" and that a series of decisions by Microsoft fostered "a corporate culture that deprioritized enterprise security investments and rigorous risk management."
The review adds that Microsoft's security culture requires "an overhaul, particularly in light of the company's centrality in the technology ecosystem and the level of trust customers place in the company to protect their data and operations."
Other recommendations include Microsoft's CEO and board of directors directly focusing on security culture, and developing and sharing a plan to make security-focused reforms across the business. Furthermore, company leadership should consider directing internal Microsoft teams to deprioritize feature developments across the company's cloud infrastructure and product suite until substantial security improvements have been made.
The report also states that there isn't definite evidence on how the hacker obtained the 2016 Microsoft Services Account (MSA) signing key, which should have been revoked in March 2021.
The Windows maker was further criticized for how long it took to correct its initial statements regarding the attack. Microsoft said in September 2023 that the incident was due to a cryptographic key being present in a crash dump. Microsoft didn't amend that post until March 12, when it admitted no crash dump containing the key had been found.
"Our leading hypothesis remains that operational errors resulted in key material leaving the secure token signing environment that was subsequently accessed in a debugging environment via a compromised engineering account," Microsoft wrote in its updated post.
Microsoft has investigated 46 theories as to how the hack took place, including the hacker possessing a theoretical quantum computing capability to break public-key cryptography, and an insider who stole the key during its creation, none of which it has been able to prove.
More bad news for Microsoft came last week when The US House of Representatives issued a strict ban on congressional staffers using the company's Copilot generative AI tool over security fears