What just happened? Researchers have detailed a proof-of-concept firmware attack that can affect almost every existing Windows and Linux device from virtually all hardware vendors. While the vulnerabilities are believed to have existed in the UEFI software for decades, the attack was only highlighted earlier this week at the Black Hat Security Conference in London.
Named 'LogoFAIL' by the researchers who created it, the exploit is said to be very easy to implement, potentially leaving users vulnerable to remote attacks by malicious actors. It is the combination of around two dozen vulnerabilities that were only recently discovered by cybersecurity researchers but are believed to have existed within virtually all UEFI from the major vendors for years.
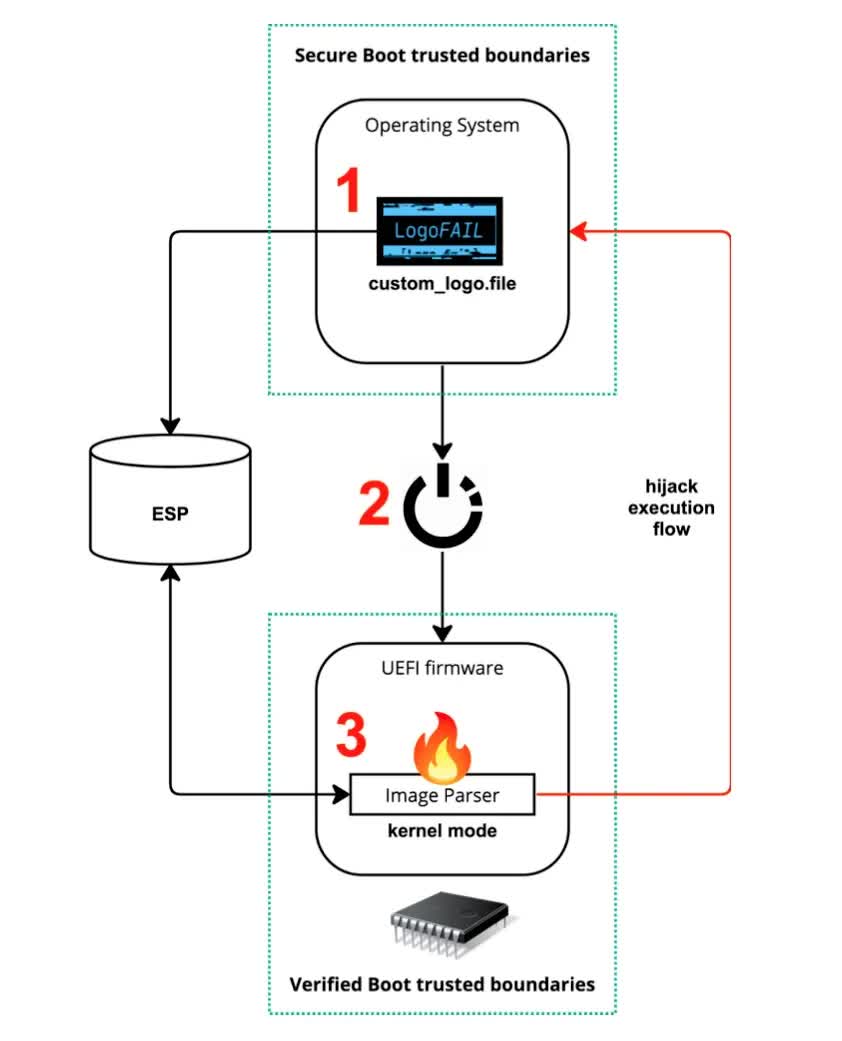
According to the researchers, LogoFAIL enables attackers to replace the legitimate logos of OEMs with identical malicious images by exploiting a dozen critical vulnerabilities in UEFIs from all three major independent BIOS vendors. The fake logos are specifically designed to exploit the vulnerabilities and allow attackers to execute malicious code remotely at the earliest stage of the device's boot process, or Driver Execution Environment (DXE).
Once the arbitrary code is executed, attackers gain "full control over the memory and the disk of the target device, thus including the operating system that will be started." LogoFAIL will then deliver a second-stage malicious payload even before the OS is booted. Attackers can exploit the vulnerability either by remotely exploiting unpatched bugs in the browser, media player, or other apps on the PC, or by gaining physical access to the device to manually replace the legitimate logo image file with a malicious one.
The research was carried out by cybersecurity firm Binarly, which says both enterprise and retail consumers are vulnerable to the exploit, which can grant hackers near-complete control over users' PCs. What makes it so dangerous is that the attack can be remotely executed in some cases by using methods that cannot be detected by traditional security software.
The exploit typically runs during the early stages of the boot process, allowing the hackers to bypass the operating system's internal defense mechanisms and endpoint security products. As things stand now, no known software or hardware protection can defend against the exploit, whether it is Secure Boot or other similar features specifically designed to protect against bootkit infections.
The discovery is part of a collaborative study carried out by several companies in the x64 and Arm ecosystem, including UEFI suppliers like AMI, Insyde and Phoenix, as well as device makers like Lenovo, Dell and HP. Other major hardware companies like Intel and AMD were also part of the research initiative.